I recently completed my second of Offensive Security's 300 level courses: Evasion Techniques and Breaching Defenses (OSEP). In this post, I'll be summarising my key takeaways from the course, experience of the labs, the challenges and the exam, and my ongoing journey towards the OSCE3 certification.
Overview
The PEN-300 course is Offensive Security's latest certification course in their penetration testing stream, focusing on modern pentesting techniques such as endpoint protection bypasses (AV, CLM, AppLocker), MSSQL server attacks and Active Directory domain exploitation. Although these areas by themselves are huge and worthy of their own individual courses, the PEN-300 does a great job at covering each area in detail, both for passing the exam as well as for immediate application in your real world engagements. As a previous student of the OSCP (PWKv1), I was excited when I first heard the news that Offsec were delivering a new advanced penetration testing certification, as I had missed out on the previously revamped Active Directory material which came with the course refresh in PWKv2.
At its core, the PEN-300 is a course on modern pentesting and red teaming. The course covers current pentest techniques which can be applied to attacking Windows Active Directory environments. The course features eighteen chapters in total, each of which comes with a private lab environment for trying out techniques and developing tools. In the first half, the PEN-300 familiarises the student with modern endpoint defenses and explores how they can be bypassed using custom developed tradecraft. As the course goes on, it combines the initial content from the earlier modules and situates them within small Active Directory environments, allowing the student to apply the techniques and tradecraft they have learned to increasingly challenging scenarios. Towards the end of the course, the student learns how to attack and compromise a realistic Active Directory environment, which is where the course's utility really comes in. For additional information, the complete syllabus for the course can be found on the Offensive Security website here.
Pricing
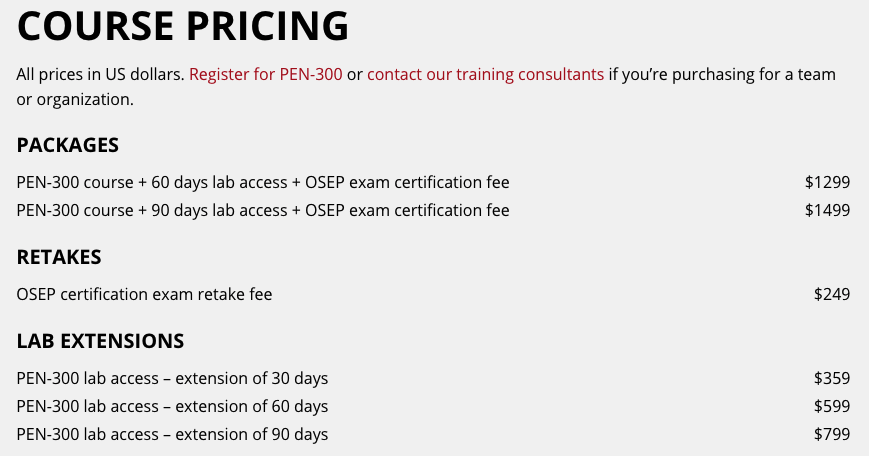
The pricing for OSEP is in line with the other 300-level courses, all of which come with a minimum of 60 days lab time (200-level courses initally begin with 30 days). Based on the sheer amount of content and my initial goal to complete all of the extra miles and challenges in good time, I opted for 90 days of lab time. Overall, this was enough time to go over the majority of the content twice over, and create clear chapter notes, hint sheets and code snippets which I could reference both during the exam and whilst conducting real world pentesting engagements.
The course pricing as per the Offsec website is below:
Pre-reqs and prior knowledge
In the course description, Offensive Security indicates that candidates who have initially taken PEN-200 (PWKv2/OSCP) are equipped to jump right into PEN-300.
If you haven't completed PEN-200, or, like me, you took the course prior to the PWKv2 update in 2020, you may have missed out on some of the Active Directory attack vectors covered in the refreshed content. In my personal experience, this didn't cause any real blockers when progressing onto PEN-300, as the Active Directory attack paths are well explained from the bottom up, beginning with a base explanation of key concepts such as Kerberos and domain trust relationships. If you want to brush up on Active Directory before jumping into PEN-300, a great starting point is with the CRTP and CRTE courses from Pentester Academy.
As for the other main focuses of PEN-300, namely the C# and PowerShell sections, it does help to have some general programming experience as well as basic knowledge of Win32 APIs. This is by no means a requirement though as the course will bring you up to speed, but your mileage may vary based on concepts you've already encountered. This will help particularly when you are developing your own custom tradecraft.
Another thing worth mentioning is that the PEN-300 teaches all of its attacks and techniques using Metasploit as its primary C2 platform. Other freely available platforms such as Covenant and PoshC2 are mentioned in extra mile exercises, and are a nice way of getting the student to adapt what they have learned to other platforms. It is also permitted to use any open-source, freely available C2 platform in the exam (commercial platforms such as CS are strictly disallowed) but for simplicity's sake I stuck with Metasploit.
Finally, whilst it isn't really a core focus, there are several chapters which cover Linux exploitation. As the course is centred around understanding how to attack Active Directory, Linux can also feature in varying capacities. I personally do not spend much time attacking Linux in my day-to-day work, so this was a welcome topic to learn more about. This said, don't expect to be pulling off headache-inducing OSCP-esque privilege escalations (pain, sufferance etc.). Instead, PEN-300 looks more at how Linux can be used to pivot across a domain or gain access to user credentials, using its built-in support for SSH and Kerberos.
What will you learn?
The PEN-300 covers a complete set of technical skills you can expect to use on an internal pentest. As a large component of the course is on evasion techniques, you spend time writing PowerShell and C# code using Microsoft Visual Studio. This includes developing custom shellcode runners and crypters, MSSQL enumeration tools, AppLocker and AMSI bypasses and fileless lateral movement tools. I found that writing the code helps to understand step by step how each technique works, with the added benefit of evading signature-based detection which perhaps some of the more popular tools would fall victim to.
Besides the majority of modules being on Active Directory and Windows, PEN-300 includes several sections on exploiting Linux (post-exploitation, lateral movement) and performing kiosk breakouts. Generally I felt that these modules were a welcome change in direction and help tie the core material together. In particular, whilst I didn't find the kiosk breakout module to be too applicable to my current line of work, I found the content enjoyable, as there are plenty of real-world systems which the techniques could be applied to. There is also other content such as the bypassing network filters module, which is perhaps better suited to performing a real engagement as it covers areas such as domain fronting, DNS tunneling and IDS/IPS sensors.
Having gone into PEN-300 with a fairly decent understanding of Active Directory attacks, I would say the biggest takeaways for me were around developing C# code and leveraging Metasploit as a C2 platform. Having had no previous experience of commercial C2 platforms such as Cobalt Strike, PEN-300 helped me get very comfortable with attacking domains whilst managing several Meterpreter sessions in a clean way. If you are also looking to gain experience using Cobalt Strike, and want to bridge this gap in tooling, PEN-300 also works as a nice segue into CRTO, which I am currently working on.
Extra miles
PEN-300 features extra mile exercises for most chapters in the course. Compared to OSWE, I didn't find these to be as challenging or to require as much time spent doing extensive research, as they were largely a continuation of the exercise. For instance, you might have an exercise to develop an alternative bypass method, or port a C# technique into PowerShell. A typical extra mile could entail finding an alternative way to achieve the same outcome, or to implement a particular technique in a different language or payload format. This is useful, as during a red team or pentest, you may need to quickly adapt your payload or bypass technique to suit a change in execution context. It is also useful to have a few extra tricks up your sleeve in case your go-to techniques are detected. During OSWE, I felt that the extra mile exercises could take from an hour to a whole week to complete, but overall OSEP felt more uniform. For your own knowledge of techniques, and for the sake of the challenges and the exam, I would recommend completing as many as you can; particularly the ones related to the AD attack chapters.
Challenges
The challenges for me were the highlight of the course. There are six are in total, all of which feature specific objectives set within a simulated AD environment which draw upon the techniques taught across multiple chapters in the course. Each of these challenges feature a set of flags to collect, which indicate a partial (local.txt) or full compromise (proof.txt) of each machine. The first three challenges are centred more on testing specific technique areas, with the final three having a marked increase in difficulty, and more of an emphasis on chaining techniques together. The challenges are a great way of testing what you have learned and identifying any areas which you may need to practice or improve your tradecraft around. Across all six challenges, you will cover the skills you need to obtain the certification, with the final two bearing the closest resemblance to the exam. As you go along, I would recommend going through them several times and keeping step-by-step notes of your attack path, including commands, screenshots and flags you capture. It's useful to do this in line with the exam guidelines to get you used to the reporting requirements, but also for the general purpose of cleanly documenting things that you have tried which worked and failed. This will pay off big time when it comes to the exam, as you will save a tonne of time on reporting. It's also worth using slightly different techniques or payloads on consecutive tries, to check that there aren't any gaping holes in your tradecraft for when you take on the exam.
OSEP exam
The certification exam is another 48-hour long proctored assessment, topped off with 24-hours to report on your findings. Without giving the game away, my best advice is to keep things simple, be comfortable with adapting your tradecraft and perform thorough enumeration. If you have been through and completed all of the challenges prior to sitting the exam, you will be in the right mindset and know everything needed to pass. 48 hours is a reasonable amount of time to complete all of the exam objectives and complete the report, provided that you take adequate notes and gather evidence as you go along. I used the macOS version of Obsidian to organise my notes and hint sheets, and in my experience it is probably the best notetaking tool I've come across.
The exam itself follows along from the challenges, and is comparable in difficulty to challenge six, with a few curve balls thrown in along the way. It is key that you apply a solid and repeatable methodology whenever you come across a new piece of information. For instance, repeat your local and domain enumeration each time you compromise a new machine or user. As the course is supposed to prepare you for real world engagements, go in with a mindset around misconfigurations or oversights you may have seen before on a company network. The key is to think in simple terms and use your tooling to fill in the gaps. Tools such as PowerView and BloodHound really prove their worth here. As the focus is not necessarily on being stealthy, you are free to use them to your heart's content.
General tips
In no particular order, the following is a list of general hints and tips I picked up along the way:
- Take notes on each of the chapters using Obsidian, or similar editor.
- Create a separate hint sheet with PowerShell oneliners, code snippets, command line arguments, and general tool syntax. Obsidian has a great lookup feature which you can use to pivot to any information you need with Ctrl/Cmd+O.
- Set up a private GitHub repository of all the code you wrote during the course for easy reference.
- Try to obfuscate your payloads to have as few detections as possible according to AntiScan.Me. Ideally, go into the exam with a set of full undetectable EXE/VBA Meterpreter payloads.
- Be prepared to use an alternative tool or technique in the event that your go-to one fails. For instance, if you land on a machine with AppLocker and/or Constrained Language Mode enabled, have a C# executable ready to go.
- If you are coming into the course from a pentesting background but have limited Active Directory experience, it could be worth jumping into CRTP or CRTE from Pentester Academy to brush up on your knowledge.
- Read alternative sources on Active Directory to fill in any gaps, and seek out different ways of doing things. Some of my favourites include ired.team and HackTricks. Bookmark anything useful you stumble upon during the course so you can easily find them later.
- Develop a thorough, repeatable enumeration methodology. Repeat this every time you compromise a machine or user. For example, if you compromise a new user, spray their credentials across the domain. In the case of a computer, review the running processes and dump credentials, determine its execution rights etc.
What’s next?
Before jumping straight down the rabbit (or fox?) hole with OSED, I'm continuing my learning path through Active Directory with the newly updated CRTO course by Zero Point Security. I'm pretty excited to be using Cobalt Strike now that it is freely available within the labs, and look forward to eventually using it on real world penetration tests and red team engagements. My plan is to wrap up the end of 2021 by starting OSED, hopefully completing the OSCE3 this coming Winter.
